As many of you are concerned with blockchain being hacked, we will dive into the core of the issues to understand whether this type of scenario is even possible.
We are living in a world where security is a huge concern, and data breaches happen to be a daily activity. The internet infrastructure that we use nowadays is becoming obsolete day by day. It can’t clearly prevent any kind of high-end cyber-attacks. No matter what type of cybersecurity we are using, it definitely can’t protect us 100%.
Blockchain technology happens to promise a different approach in this manner. It ensures that we no longer have to depend on trust and can control our digital content ourselves. Moreover, in a way, many claim that no one can hack the blockchain. But is that statement really true?
Is there no way one can hack blockchain? In reality, blockchain is awfully powerful and can seem like no one can hack blockchain. However, we have to say, it’s not entirely immune to attacks. Every single technology comes with strong and weak points. Thus, we’ll be digging a little deeper and let you know can blockchain be hacked or not.
But before we begin, let’s check out a few of the major blockchain hack online that happened over the years. So, let’s start!
Enroll Now: Certified Blockchain Security Expert (CBSE) course
Blockchain Hacked: Can You Hack Blockchain?
First Blockchain hack online in June 2011.
Loss: $50,000 (2609 BTC)
This is one of the well-known blockchain hacked scenario in history. Apparently, the cyber-criminal got ahold of the auditor’s credentials and then misused those to get into the system. More so, the attacker then changed the value of 1 BTC to 1 cent. Furthermore, the attacker also collected 2609 BTC from multiple clients that sold the BTC at this very low price.
After that, he/she even purchased back 650 BTCs from another account as well. After the hacking blockchain scenario came to light, Mt. Gox stopped all operations for a couple of days. However, then they restarted the operations and carried on.
Now, let’s move on to the next attack of this can you hack the blockchain guide.
Read More: Blockchain Demo Alternatives – A Must Read Guide
Second Blockchain hacked in March 2014.
Loss: $350 million (750,000 BTC)
The second attack was even worse for Mt. Gox. Apparently, this time, the attacker found out about a bug in the codes and saw that transactions are more flexible. More so, anyone could edit the detail of the transaction and make it look like that it never even happened. So, kind of like double-spending.
If we go into more detail, the process happened like this. The attacker manipulated the sender’s signature before it was stored permanently in the ledger. He/she also changed the transaction ID. The new ID and changed transaction can overwrite the original transaction details and make it look like that the receiver didn’t get any funds.
However, in reality, the attacker did receive it, but the system mistook it for an unsuccessful transaction. Once it’s done, the attacker then asked for the transfer again and got the funds two times.
This time Mt. Gox halted all of the BTC transactions immediately after the detection of the cyber-attack. More so, there were no refunds as well. After some time, they couldn’t cope with the loss and then filed for bankruptcy.
Overall Loss: $430,000 (122,000 BTC)
First Blockchain hack online in March 2012.
In the first one, the attacker mainly attacked Bitcoinica’s hot wallet and decrypted it from Linode’s server. In the end, the attack took about 43,554 BTC. Other users who were also using Linode’s server got hacked too.
The Second Blockchain hacked in May 2012.
Well, the first time wasn’t enough for Bitcoinica. The second time, the attacker got into the internal system of the database. From there, he/she stole all the users’ private information and even took 38,000 BTC.
Third Blockchain hack in July 2012.
The attacks got so bad that, that later on in July, they stole around 40,000 BTC again! However, they happen to store their funds secretly in Mt. Gox secretly, and they were later refunded.
Let’s move on to the next one in this can you hack blockchain guide.
Blockchain hack online in August 2016.
Loss: $72 million (120,000 BTC)
The story is quite short in this one. Bitfinex started to use BitGo’s multi-signature wallet just a year ago before the attack. Apparently, the wallet had some major issues, and there were some massive vulnerabilities in it. In reality, the attacker found the issue and stole the BTCs.
After the attack, the company quickly issued BFX tokens for compensating their customers. BFX tokens are redeemable in USD. However, they refunded all the stolen money gradually as it was a hefty sum. With just this one attack, the price dropped from $607 to $515 within just a few hours!!!
Blockchain hack online on 6th December 2017.
Loss: $80 million (4700 BTC)
It’s more of a recent attack on blockchain. Apparently, the Slovenian exchange platform, NiceHash, was hacked. Soon after the blockchain hack, the CEO came into Facebook Live and announced it. However, he didn’t get into much more detail.
All we know so far that one of their employee’s computers was compromised, and the attackers used that to steal the coins.
In reality, the company suspended all the transactions for the next 24 hours to analyze the issue and how they can prevent it from ever happening again. We have to say, it’s a rather good initiative from the company management.
So, these are some of the blockchain hacks that happened in the past. Now, let’s move on to the next segment of this can you hack blockchain guide.
Hacking Blockchain: Possible Scenarios
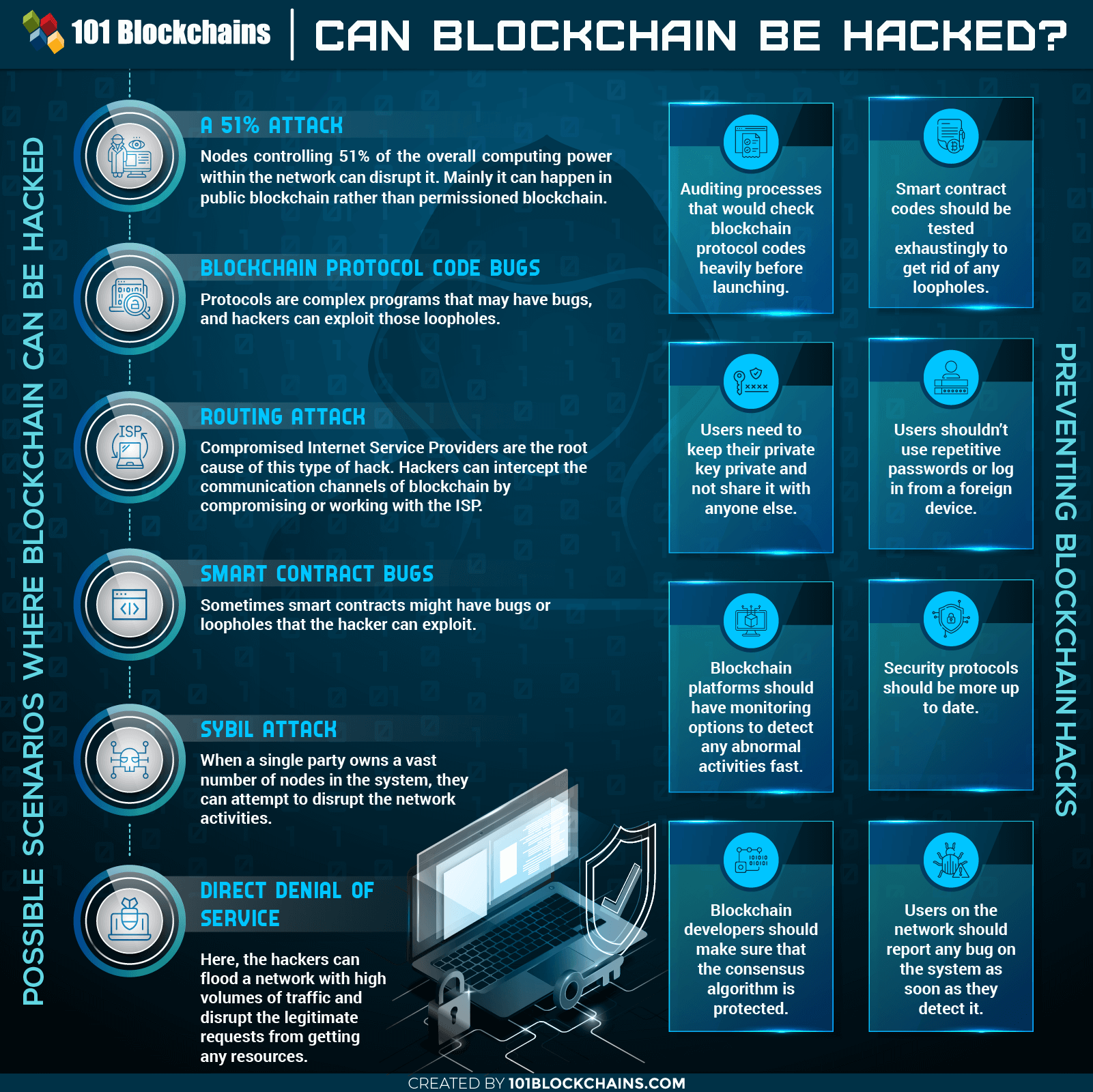
Please include attribution to 101blockchains.com with this graphic. <a href="https://101blockchains.com/blockchain-infographics/"> <img src="https://101blockchains.com/wp-content/uploads/2019/10/Can-blockchain-be-hacked.png" alt="Can blockchain be hacked="0' /> </a>
Now we’ll discuss if blockchain can be hacked and, if so, how it can be possible. Some specific scenarios may occur. Let’s see what they are –
Let’s start off with the basic hacking blockchain scenario. If you have been dealing with blockchain for enterprise some time, then you must have heard about the 51% attack scheme. But how can a 51% attack happen?
Let’s say there’s a public blockchain or DLT that uses Proof of Work consensus and happens to have a good amount of active nodes. Moreover, all of the nodes tend to have special software and hardware tools for mining because that’s how you validate a transaction in PoW.
The rule of this type of network is full decentralization. So, users would not be part of a group and would follow all the rules of the system. Furthermore, to make sure the decentralized nature prevails, every node offers a computation power but not enough to overpower anyone else.
However, if a hacker can use a blockchain hack tool to get more computing power, then he can launch an attack. But to do that, he needs to control 51% of the overall computational power within the system. By doing so, they can higher hash rate compared to other nodes.
In the long run, they can manipulate the transaction process, and that would lead to double spend. However, this will only occur in power-hungry consensus algorithms that deal with computational powers.
Can Hackers Pull It Off?
In reality, public blockchains such as Ethereum comes with a high number of nodes. The more nodes the network adds up, the more computational power is needed. Additionally, new nodes are adding to the network every single day.
This high level of computational power ensures that hacking blockchain would be a rather tricky task. Mainly because the blockchain hack tool they’ll be using isn’t capable of offering this much computational power to overcome other nodes.
Also, any platform not using PoW is on the safe side, and if it’s private or federated, then you’re in the clear for sure.
Not so popular public blockchains can be the main target here. In 2018, the hackers tried to pull a 51% hack blockchain attack on Monacoin, Verge, etc.
Read More: PoW Vs. PoS: A Comparison Between Two Blockchain Consensus Algorithms
Does It Benefit the Hackers in Any Way?
If a public blockchain isn’t that popular, then the value of its cryptocurrency would be low. Through a 51% attack, they would undoubtedly get coins, but the profit would be much lower. On the other hand, the hacking blockchain of a popular public platform would require a considerable number of computational powers, and in the long run, it would cost more than the profit.
-
Blockchain Protocol Code Bugs
Another example in this hack blockchain guide would be any flaws in the protocol source codes. Well, the blockchain is a complicated system, and that can have bugs in the protocol codes, as well. Let’s see an example of this issue to understand it better. This is one of the disadvantages of blockchain.
There was a blockchain hack scenario in 2010, where they misused a bad code in the Bitcoin protocol. In reality, the code that checked Bitcoin transactions were faulty. Apparently, the code doesn’t work if the outcome is too large, and it causes an overflow in summing up.
As a result, a hacker used it to his/her advantage and generated 184.467 billion coins. However, the maximum supply of Bitcoins is actually 21 million! After finding out, the creator Satoshi Nakamoto and another developer Gavin Andersen quickly fixed the issues within just a few hours.
Furthermore, they forked the bad chain to create a good chain and advised other users to avoid the chain created by the hacker. All in all, it was a good save.
But we have to say, someone doing a similar hack blockchain scheme using the same method is quite unpredictable at present.
Anyone wanting to attack using a bug like this has to have an advanced level of skills even to identify the issue, let alone make changes to it. As blockchain is a sophisticated platform, it’s quite impossible.
Also, now, blockchain developers thoroughly check their codes before launching, and that prevents this kind of a mess effectively.
Enroll Now: Certified Enterprise Blockchain Professional (CEBP)
This is another faulty code situation that can lead to hack blockchain scenarios. It’s more of a hacking a program in the network rather than the whole platform itself. However, this kind of blockchain hack can leave a serious impact.
Smart contracts are awfully popular and run on quite a lot of blockchain platforms. If you predefine the conditions, it can transfer assets based on those rules. Also, as they are on the blockchain, then no one can modify them once the terms are set.
Furthermore, after all, conditions are met, it can execute automatically, and those also get a permanent place in the ledger. So, no one can actually reverse the execution. However, if somehow, the smart contract code is full of bugs, then hackers may exploit that.
A good example would be the attack on DAO. During 2016, the Ethereum community created DAO to govern investment funds and help them better manage proposals. However, they were using smart contracts to manage the DAO.
Even though the Ethereum system protocol was working perfectly, the smart contract program had a bug. In reality, the bug allowed a user to request money from the DAO account and not record it on the ledger. This type of DAO hack poses a great threat to blockchain security.
Hacker got hold of it and took $60 million from the network. After this incident, Ethereum hard forked to reset the system. So, the Ethereum you see now is actually the result of that hard fork. However, some people still use the old chain, and that’s called Ethereum Classic.
In terms of these, other questions such as can blockchain wallets be hacked or other services relating to blockchain be hacked rise. We have to say, it’s the same for everything else as well.
Want to know more about Ethereum? Enroll Now: Ethereum Development Fundamentals
It’s another kind of attack where an entity can have a huge number of nodes within a single network. With the number of nodes, the entity can attempt to flood the network with bad transactions or invalid ones and disrupt the activity.
Hackers can use the various blockchain hack tool for this one. However, you have to know this attack is still theoretical. However, preventing it is much simpler. If the enterprise blockchain platforms can make owning a massive number of nodes expensive using protocols and algorithms, then we can safely say the hackers can’t launch an attack.
It’s more of an internal attack rather than coming from the outside. A compromised Internet Service Provider is the root cause of this type of hack. Hackers can intercept the communication channels of blockchain by compromising or working with the ISP.
Even though it’s possible to run nodes from anywhere in the world, however, in the current situation, running nodes is awfully centralized. These ISPs tend to carry out the load of the traffics, and these entry points are vulnerable.
Intercepting signals on these channels would disrupt the communication and can then manipulate the transaction process. Also, hackers can partition the network into separate pieces and spend coins on the good in one of those. Later, when they remove the partition, the smaller chain would get automatically canceled.
As far as it goes, there have been no reports of such attacks so far.
Here, the hackers can flood a network with high volumes of traffic and disrupt the legitimate requests from getting any resources. We think you see this kind of attack on a daily basis on centralized enterprises.
In reality, the method is to keep sending a large number of requests to the company’s server, not giving it time to cope with the increased traffic surge. As a result, the bandwidth runs out, and the server crashes.
However, WE would like to point out, hackers can’t actually steal anything rather than just causing harm to the network activity. More so, many blockchain solutions can safeguard it from this kind of attack efficiently.
Read More: Top 5 Blockchain Smart Contract Examples
Hacking the Blockchain or Crypto Exchanges?
As you already saw that most of the examples of hacking the blockchain are mainly of a crypto exchange or any platform that happens to offer cryptocurrencies. Thus, most of the newcomers tend to confuse these crypto exchange hacks and hack blockchain.
However, you have to know there’s a bit of difference between these two. Let’s see why they are different –
In reality, most of the public blockchains have very different technology architecture than each other. And so, they aren’t interoperable. Therefore, you can’t actually transact on the bitcoin platform using Ethereum.
Thus, this is where the crypto exchanges come into play. In reality, these offer you a platform where you can use almost any kind of cryptocurrency. You can even convert a cryptocurrency into another. Even though they make it easier, however, they are third-party service providers.
Thus, trading is very easy; however, they don’t have the necessary amount of security for their centralized servers. And this way, hackers using blockchain hack tool can easily hack these tokens without any issues. In reality, you can find blockchain risks once you start to use it.
However, when they do attack these crypto exchanges, it doesn’t mean that they are hacking the blockchain. Instead, it’s just an attack on the central server and isn’t considered hacking the blockchain technology.
Let’s move onto our next segment in this can blockchain be hacked guide.
Users Are Equally to Blame or Even More!
When someone asks, “can blockchain be hacked,” the answer would be between a grey area. However, in every case, you’ll see that in most cases, users are to blame, and sometimes they are the whole reason why blockchain hack happens in the first place.
In reality, blockchain technology does offer quite a robust system, and there have been only a few successful cases of a hack blockchain situation. However, most times, users lose a vast amount of money. But how?
Well, the security in blockchain technology is quite robust, to begin with. However, you are forgetting about the most vulnerable entry point of the system – the users.
You might be thinking, can blockchain wallet be hacked, and I’d have to say – YES!
Various entry points such as exchanges, wallets, other third-party services that the users use tend to have a vulnerable security protocol. Also, many users don’t even the difference between a private key and a public key. Therefore, they can reveal their private keys to others and lose all of their assets.
Curious about the differences between private and public keys? Here’s a guide to private key vs public key.
Thus, hackers can easily use a blockchain hack tool to hack into the system and steal millions of assets.
We have to say that most of the scenarios that we included in this hack blockchain guide are theoretical. Even so that that blockchain platforms are defending these without any issues in real-time. The high level of crypto hacking mainly happened because, well, humans aren’t’ so great at being vigilant.
Many users tend to reuse passwords, operate the internet carelessly, fall victim to phishing scams, neglect any unusual behaviors, use their devices in vulnerable places, and so on. All of these can lead to hack blockchain schemes quite easily.
Also Check: Understanding European Blockchain Services Infrastructure (EBSI)
Can You Really Defeat the Hackers?
There are many recent startups and enterprises that are addressing the issue of blockchain hacks. Moreover, there are some definitive ways to improve the overall security of the architecture. However, developers and users both have a huge play in this. More so, blockchain features undoubtedly can help out in defeating the hacker if you use it in the right way. Let’s see what these are –
- Auditing – Auditing processes that would check blockchain protocol codes heavily before launching. Any kind of false or bad code would be detected quite easily. More so, if you can bring AI into the mix, it would be highly accurate.
- Test Exhaustively – Smart contract codes should be tested exhaustingly to get rid of any loopholes. Without thousands of real-time tests, no one can figure if it has any bugs or not.
- Privacy – Users need to keep their private key private and not share it with anyone else. There’s actually no telling from where your private keys can leak. So, keep it in a safe place away from everyone else.
- Vigilance – Users shouldn’t use repetitive passwords or log in from a foreign device. It would give a hacker a chance to misuse your account.
- Monitoring Options – Blockchain platforms should have monitoring options to detect any abnormal activities fast.
- Up-to-date – Blockchain Security protocols should be up-to-date as fast as possible. It will ensure that there would be no vulnerability from the software point of view.
- Consensus Algorithms – Blockchain should use anti-hack consensus algorithms.
- Constant Reports – Users on the network should report any bug on the system as soon as they detect it. If the users treat the system as their own, then it would stay secured for them as well.
Enroll Now: Certified Enterprise Blockchain Architect (CEBA)
Ending Note
Well, can blockchain be hacked or not is a rather complicated question, to begin with? The technology itself is far more superior to any others out there so far. And as we know, it’s still quite new to the tech club. Thus, it will definitely have some flaws as well.
However, most of its flaws can be overcome if blockchain companies start to consider quality over quantity.
On that note, many enterprise blockchains now offer the highest level of security without all the flaws. And they do seem quite promising so far. Hopefully, these platforms can fend of hack blockchain situations without any issues.
Now that you know about the risks, what are your next steps? Do you want to become a blockchain security expert in dealing with all these issues? Enroll in our Certified Blockchain Security Expert (CBSE) course and learn how to resolve all the security issues at once!
 Extra Crypto Extra step for latest news
Extra Crypto Extra step for latest news
